Information security is a hot button issue these days, with cyber terrorists, spies, and computer hackers stealing highly sensitive and confidential information online – and making front-page news in the process.
What is Information Security?
Information security (or “InfoSec,” for short) is the practice of defending data confidentiality and computer networks from unauthorized use or attack. Also known as computer security or network security, InfoSec protects computer networks both large (a Fortune 500 company, for example) and small (a home computer or personal smart phone).
Most governments, militaries, corporations, organizations and private businesses store important data about their employees, customers, products, research and finances on electronic computer systems connected to a single, or multiple networks. In addition to protecting confidential or proprietary data, an organization may be required to use InfoSec protocols for legal or ethical reasons (for example, an insurance company needing to protect customers’ private health information according to HIPAA laws). Or, banks that keep our financial records protected.
We know cyberattacks hit businesses every day.i Because private information may be vulnerable to theft, damage or public dissemination by hackers and competitors, many organizations employ information security specialists to help protect their computer systems and networks.
3 Domains of Information Security
There are three main domains of information security which ultimately aim to protect, detect and respond to any type of compromise.ii
- Cyber (computer, network and information security, firewalls and countermeasures)
- Physical (the wires, silicon, glass and constructs)
- People (employees, consultants, suppliers, partners)
Many who pursue a career in information security start out with a propensity for one of these domains. They then study relevant theories and methods to fine tune appropriate hi-tech computer or tactical managerial skills and knowledge.
DID YOU KNOW? The Bureau of Labor Statistics predicts that employment of information security analysts in the area of computer systems design will grow by 56 percent from 2016 to 2026.iii
Information Security vs Cybersecurity
The two terms “Cyber Security” and “Information Security” are generally used as synonyms in security terminology, because there is overlap, however there are some key differences.
- First off, information = data with meaning (analog and digital). The numbers 1234567 can be random but not if assigned as a credit card number. InfoSec is all about protecting this type of information. Information security analysts therefore focus on the confidentiality, integrity, availability (CIA) of the information
- Cyber security is about securing things that are vulnerable in the cyber realm. It considers where data is stored, and technologies used to secure the data (hardware and software). If you are a cybersecurity professional, you are highly focused on the strategies that go into protecting data in cyberspace from unauthorized access
8 Interesting Facts about Information Security
Hackers may seem like an invisible enemy, but they pose legitimate threats to consumers and organizations everywhere. You may be surprised to learn about the toll information and cyber security threats take on their victims.
- Identity theft is one of the most common outcomes from data breaches. The Federal Trade Commission’s Consumer Sentinel Network Report stated that identity theft accounted for 13.87 percent of all consumer complaints in 2017iv
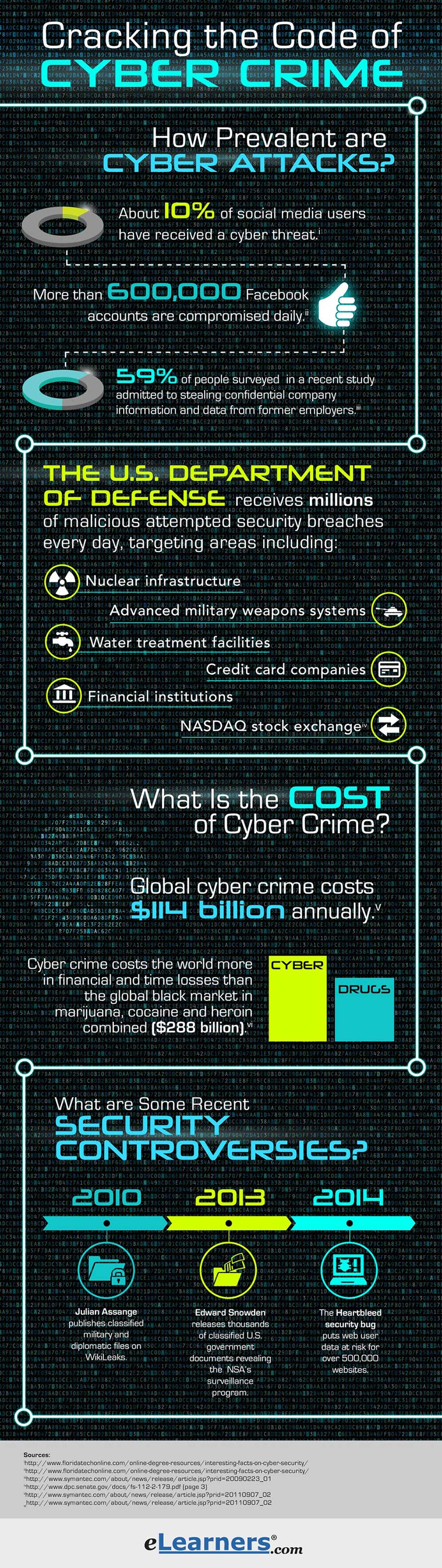
- Cyber incidents cost consumers billions of dollars every year. Last year, Cybersecurity Ventures predicted that cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015.vExperts say this invisible bank robbery amounts to more money than the global trade of all major illegal drugs combined
- Cyberattacks are the fastest-growing crime in the U.S. and increasing in size, complexity and cost. The U.S. Department of Defense (DoD) receives millions of attempted breaches by malicious cyber actors every day, including attempted attacks against America’s nuclear infrastructure, advanced military weapons systems, water treatment facilities, credit card companies, financial institutions and the NASDAQ stock exchangevi
- The FBI estimates that ransomware infected more than 100,000 computers a day around the world as recently as October 2017vii
- Hundreds of thousands — and possibly millions — of people can now be hacked via their wirelessly connected and digitally monitored implantable medical devices (IMDs). This includes cardio-verter defibrillators (ICD), pacemakers, deep brain neuro-stimulators, insulin pumps, ear tubes, and more. iv
- 59 percent of people surveyed in a Symantec Corp. study admitted to stealing confidential company information and data from their former employersviii
- 53 percent of cyberattacks resulted in damages of $500,000 or morei
- About 87 million Facebook users were affected by the Cambridge Analytica data scape in the U.S. aloneix
Information Security: 12 Major Security Breaches in The News
Major advances in computer and internet technology are changing the way humans communicate and conduct business. However, an increasingly digitized world goes hand in hand with computer hacking, cyber espionage, malware, and other major security breaches that can impact millions of people across the world.
Several recent incidents have thrust information security to the forefront of international news and politics. The list of headline-making security breaches continues to grow. Here are a dozen alarming incidents from the not so distant past.
- By far the biggest data breach in history is in 2013-14 when 3 billion Yahoo users are hacked in a data theft. The investigation into the cybercrime underscored how difficult it was for companies to get ahead of hackers.xWe now know in 2018 there is a hacker attack every 39 seconds that affects 1 in 3 Americans each year xi
- In 2016 two Russian-backed groups called "Cozy Bear" and "Fancy Bear" tunneled into the DNC’s computer system. The Department of Homeland Security and the Office of National Intelligence on Election Security issues statements in 2017 that they are confident the Russian Government is behind the cyberattacks. Information continues to evolvexii
- In 2017, security researchers detect that Russian hackers had infiltrated and probed U.S. power companies. there was even evidence that the perpetrators had direct access to an American utility's control systemsxiii
- The Cambridge Analytica scandal rocks the social media world in 2017 when it is found that about 87 million users on Facebook had their public profile data scraped by third-party apps. The vast majority of affected users were in the U.S.ix
- The cyberattack on the Equifax credit reporting agency in 2017 led to the theft of Social Security numbers, birth dates, and other data on almost half the U.S. populationxiv
- In 2018 Under Armor experiences one of the largest cyberattacks on record. 150 million users of its app, MyFitnessPal, had their information acquired by an unauthorized party xiv
- The U.S. Justice Department uncovers a major government-backed Iranian cyber-espionage ring. These hackers broke into the computer networks of 144 U.S. universities, stole 31 terabytes of intellectual property and caused f $3.4 billion worth of damages. They also attacked 36 private American companies and infiltrated five U.S. government agencies, stealing the emails associated with thousands of accounts xiv
- Hudson’s Bay Company who owns Saks Fifth Avenue and Lord & Taylor Inc confirms a massive hack in April 201 They report hackers stole the data of more than 5 million credit and debit cards xiv
- Ticketfly, a subsidiary of Eventbrite concert ticketing agency announces in June 2018 a data breach that impacted more than 26 million customer accounts. The stolen information included customer names, addresses, email addresses, and telephone numbers xiv
- In 2018, the U.S. Airforce is hacked by an amateur hacker who illegally accessed an Air Force captain’s computer by exploiting a known security flaw, and stole classified information about MQ-9A Reaper drones and their operators. The hacker then tried to sell them on the dark web for just $150xiv
- Even children’s data is stolen. In 2018, a cyberattack on electronic toymaker VTech Technologies exposed the personal data of 6.4 million children. Plus, VTech failed to get verifiable parental consent before they collected this data from children - including their name, gender, birth date and more xiv
- Criminals gained access to a family-owned delicatessen chain called Jason’s Deli. With 275 locations across 28 states, the company, in 2018, found out criminals had accessed their point-of-sale terminals and installed RAM-scraping malware to steal customers’ credit card information and sell it on the dark web xiv
One to watch for 2019: VPN Filter. At the end of May 2018, officials warned about a Russian hacking campaign that has impacted more than 500,000 routers worldwide. Basically, the attack spreads a type of malware (VPN Filter) which can do a lot of damage. Not the least of which is its capacity to be used to coordinate infected devices to create a massive botnet. It can also directly spy on and manipulate web activity on the compromised routers. The FBI is on it.
The Time is Right for an InfoSec or Cyber Security Major
Information and cyber security will continue to be a highly charged issue as more people, organizations, businesses and governments store confidential and highly-sensitive data online. Due to the growing demand for more effective information security products and protocols, now could be a great time to research an education and/or career in this exciting field.
Browse available Cybersecurity and Network Security programs here to find cyber security schools with information security degree and cyber security degree programs at all levels.
[i] cisco.com/c/en/us/products/security/common-cyberattacks.html | [ii] thesecurityawarenesscompany.com/2015/07/23/the-security-domains-triad-cyber-physical-people/ | [iii] bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm#tab-6 | [iv] experian.com/blogs/ask-experian/identity-theft-statistics/ | [v] cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/ | [vi] dpc.senate.gov/docs/fs-112-2-179.pdf (page 3) | [vii] justice.gov/opa/speech/deputy-attorney-general-rod-j-rosenstein-delivers-remarks-cambridge-cyber-summit | [viii] symantec.com/about/news/release/article.jsp?prid=20090223_01 | [ix] vox.com/technology/2018/4/5/17201946/facebook-warns-most-users-had-data-scraped | [x] reuters.com/article/us-yahoo-cyber/yahoo-says-all-three-billion-accounts-hacked-in-2013-data-theft-idUSKCN1C82O1 | [xi] cybintsolutions.com/cyber-security-facts-stats/ | [xii] cnn.com/2016/12/26/us/2016-presidential-campaign-hacking-fast-facts/index.html | [xiii] wired.com/story/2018-worst-hacks-so-far/ | [xiv] technologyreview.com/s/609641/six-cyber-threats-to-really-worry-about-in-2018/ |
